Censorship-Proof Blockchain DNS Systems

The Blockchain is many things. It's undoubtedly a work of genius to a problem most people don't realise even exists because we take it for granted so often. It's provoked an unstoppable wave of idealistic innovation, mostly from libertarian ideologues and tech oddballs, on top of curious sharks in the financial sector.
It's also been a magnet for suspicion, fraud, and abuse. Rightly so, in many cases. A technology which subverts 12,000 years of human history is disruptive on an existential level we aren't used to. But there's one area which is so ripe (geddit?) for reform, it's odd it's been missed to date.
Hollywood's Problem Becomes Everyone's Solution
When some horribly obnoxious person does what they tend to do - that is to say, something their nature implies they inevitably will - we find ourselves in the daily moral dilemma of to ban, or not to ban. The quagmire is intense, but the answer is always the same: despite this mob protesting otherwise, it's better to allow ugly speech in the open than allow it to fester in the dark.
The liberal doctrine of freedom of speech is a marvelous, awe-inspiring, and noble moral value. It has an unlikely detractor.

The USSR-style behaviour gleefully adopted by the Silicon Valley darlings started years ago: de-monetise, de-boost, de-platform, faux "investigations" (witchhunts); all leading to the appeasement of highly vocal special interest groups. Cleanse the public square of that we find uncomfortable.
It all leads back to one central weakness: the domain name system.
People can always find another hosting provider. They can hide hosts behind proxy services like Cloudflare. If they are banned from social media services such as a Facebook or Twitter, they can sock-puppet new accounts, or play the whack-a-mole game. If they are "disappeared" from search indices like Google or Bing, they can build them back again.
If they start dubious websites posting copies of Hollywood movies, or even, god-forbid, publish Bittorrent links to them, the moguls in Tinseltown have fallen back on cybersecurity suppliers to provide them with the ultimate remedy: forfeiture of the domains by which people arrive in the first place.
The most ubiquitous examples, are, of course, The Pirate Bay, with its 10 years of evading LA's most lawyered-up organisations; and the shithole madnesses of 8chan and Stormfront, whom even Cloudflare have had enough of. When a domain gets blocked, another one goes up; a copy of the VPS image bounces up to a new IP, and DNS points people to it.
Politics really is downstream from culture; what happens in the academic and artistic levels rolls down the sewer into the laps of ambitious apparatchiks eager to make their name by appeasing the most vocal complainers. The last to have caved too deeply in Silicon Valley is YouTube, but as it razors off the most controversial creators, they are turning to alternative services such as Minds.com or BitChute.
The latter is a fascinating example. It replaces the YouTube CDN with BitTorrent, effectively allowing its audience to host slices of everyone's videos. But as the founder puts it:
"The idea comes from seeing the increased levels of censorship by the large social media platforms in the last couple of years. Bannings, demonetization, and tweaking algorithms to send certain content into obscurity and, wanting to do something about it.”
https://turbofuture.com/internet/What-Is-BitCHUTE
Bad actors rarely sit still. When enough DNS providers get together and refuse service, we get to an infamous point of censorship. The domain name system, like the academic "peer review" system it shares an origin with, is highly vulnerable to distributed censorship. Just as peer review can act to block publication, so can DNS.
DNS: a good start, but no longer fit for purpose
In the old ARPANET days, it quickly became apparent it wasn't too practical to refer to machines via their IP addresses. It wouldn't scale. By the mid-1970s, a directory of some sort was required.
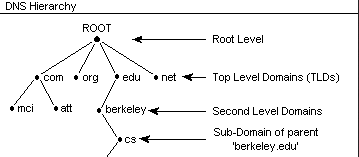
The location of a computer would be registered under a domain. Military computers would be .mil, education would be .edu, .com would be commercial, and so on. "Domain" is a word only ever used in academic circles. The structure is that of a "tree" with "nodes" (name servers) and "leaves" which divides into "zones".
10 years later, 4 UC Berkeley students came up with the Berkeley Internet Name Domain (BIND) software. Ten years after that, Microsoft imported it into Windows NT. The core of the software was NameD (name daemon).
Although the system is distributed (perhaps more so than "decentralized"), the key here in all of this is the tree has a "root" (e.g. com/edu etc). That root is subject to control. The root zone database has grown to enormous size over the last 10 years with hundreds of new top-level domains (TLDs). Even as early as 5 years ago:
"As of July 2015, it contains 1058 TLDs, including 730 generic top-level domains (gTLDs) and 301 country code top-level domains (ccTLDs) in the root domain."
https://www.iana.org/domains/root/db

The root zone file is only 2MB in size and is published as a "phonebook" of authoritative DNS servers for each TLD, by 13 root name servers labeled from the letter A to the letter M. They are operated by Verisign, the University of South California, Cogent, the University of Maryland, NASA, the Internet Systems Consortium, DISA, the US Army Research Lab, Netnod, RIPE, ICANN, and the WIDE project.
The Internet Corporation for Assigned Names and Numbers (ICANN) has "byelaws" (https://www.icann.org/resources/pages/governance/bylaws-en) for deciding who runs these root name servers. When a local "phonebook" can't find a record, it refers to another name server up the chain. Eventually, they reach the top of the tree.

Err, wait, who or what are ICANN? It has offices in Los Angeles and was devised in 1998, in California. Until 2016, it was overseen by the US government, which is a rabbit hole all on its own.
"From its founding to the present, ICANN has been formally organized as a nonprofit corporation "for charitable and public purposes" under the California Nonprofit Public Benefit Corporation Law. It is managed by a 16-member board of directors composed of eight members selected by a nominating committee on which all the constituencies of ICANN are represented; six representatives of its Supporting Organizations, sub-groups that deal with specific sections of the policies under ICANN's purview; an at-large seat filled by an at-large organization; and the President / CEO, appointed by the board."
This was never a problem before. But it is now, because nothing is off the table when it comes to political wars. Everything is up for the corruption of politicization. And we all know, all too well, where Californian sympathies lie.
One glance at their history from the most public sources gives the game away:
"In a long-running dispute, ICANN have so far declined to allow a Turkish company to purchase the .islam and .halal gTLDs, after the Organisation of Islamic Cooperation objected that the gTLDs should be administered by an organization that represents all the world’s 1.6 billion Muslims."
What?
"In May 2019 Icann decided in favor of granting exclusive administration rights to amazon.com for the .amazon gTLD after a 7 year long dispute with the Amazon Cooperation Treaty Organization (ACTO)."
Wait, what?
The individual cases don't really matter. What does, is when the world's most powerful interconnected and interdependent system is a tree hierarchy with an ultimate root, and is vulnerable to corruption and exploitation by bad actors with political plans.
Hollywood studios demanding the surrendering of domains is one thing; political actors, like China, attempting to smuggle in new protocols and paperwork to the DNS system protocols implies a new age is upon us.
Nobody voted for these people. Even if the UN took it over as previously planned, nobody voted for them either. This organisation operates as a pseudo-government but does not derive its legal authority from any known democratic process. And that's entirely understandable, because it was essentially an academic project.
However, with the problems in academia, we need to look at this again, or we need to re-factor this altogether.
Metaphysics: The Issue Of Consensus
The Blockchain solves a critical problem in human life: how to provide a mechanism for a disparate mob unable to agree on anything to reach an irrevocably provable consensus which does not depend on the parties trusting one another.
In DNS terms, what needs to be deal with now is who the publisher of the "phonebook" is and their susceptibility to interference. DNS is already used in private networks to restrict access to websites by blocking their resolution. In the UK, pornography is blocked at multiple levels, but the weak spot is the human ability to remember a domain name to go back to it.
The entire purpose of domains is to not have to remember IP addresses. If the network can't or won't resolve the human-friendly name, it takes a Herculean effort for the average person to find out how to get where they want to go.
The canonical example here is, of course, China. The 1997 "Great Firewall" (https://en.wikipedia.org/wiki/Great_Firewall) is highly adept to stop individuals accessing information the government doesn't want them to.
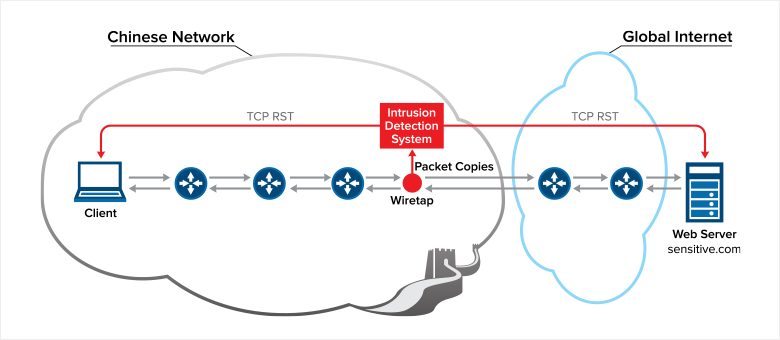
"Individuals are prohibited from using the Internet to: harm national security; disclose state secrets; or injure the interests of the state or society. Users are prohibited from using the Internet to create, replicate, retrieve, or transmit information that incites resistance to the PRC Constitution, laws, or administrative regulations; promoting the overthrow of the government or socialist system; undermining national unification; distorting the truth, spreading rumors, or destroying social order; or providing sexually suggestive material or encouraging gambling, violence, or murder. Users are prohibited from engaging in activities that harm the security of computer information networks and from using networks or changing network resources without prior approval."
Who controls the phonebook matters.
It's the same issue as the financial system: central banks control it. As long as you can trust the middleman and/or the referee, the system works. The moment it becomes corrupted or suspicious, all bets are off. We are worryingly close.
- Should Pirate Bay be blocked?
- Should Stormfront be blocked?
- Should pornography be blocked?
- Should domains be property which can be expropriated?
These are moral questions, rather than technical ones. Can they? Yes.
DNS is the last line of questioning. If your gateway blocks a site, you can use a VPN, for example, to get around it. However, if the DNS servers being used by both services collectively block a domain being resolved, you're out of luck.
Onion Routing: Only The Worst Kind of People
The first type of circumvention was the so-called "Dark Web" as the major incarnation of the Tor Network protocol, or "Onion Routing".
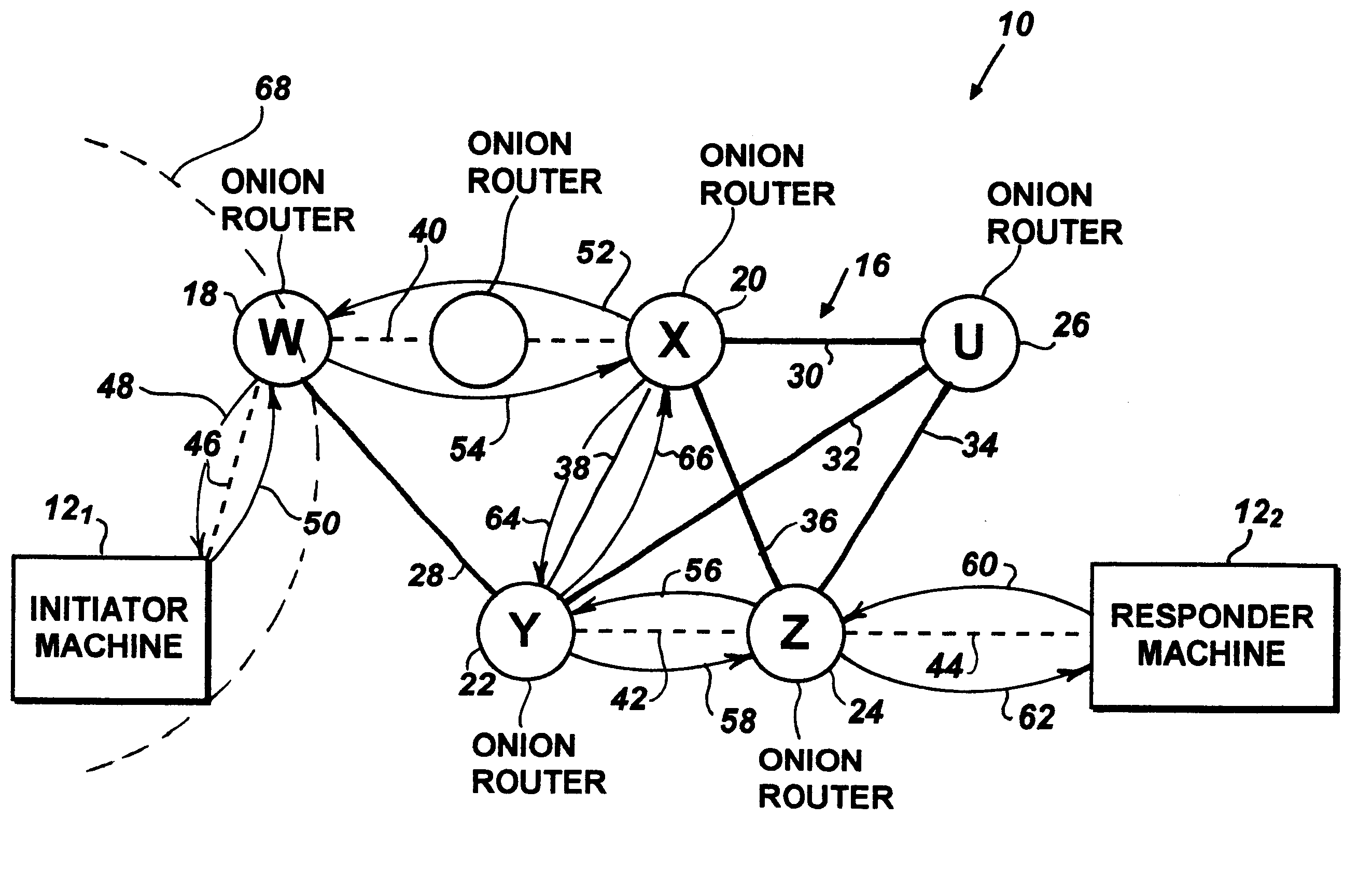
However, despite it mainly being an anti-surveillance system, it still relies on a directory of sorts which functions as a chain of nodes. Sites are available from .onion pseudo-domains which are not from the DNS root, but they rarely even remotely human-rememberable as they are generated as cryptographic hashes.
https://en.wikipedia.org/wiki/.onion
And as always happens, the first adoptees of the technology aren't the dissidents and philosophical actors being unfairly penalised, but simply the first people to have been banned from the Clearnet for doing unacceptable things. Which ultimately leads the baby being thrown out with the bathwater.
So What's The Problem If Bitcoin Already Exists?
It's not as easy as replacing the DNS "phonebook" with a blockchain. And to understand why, we need to go back into the history of DNS.
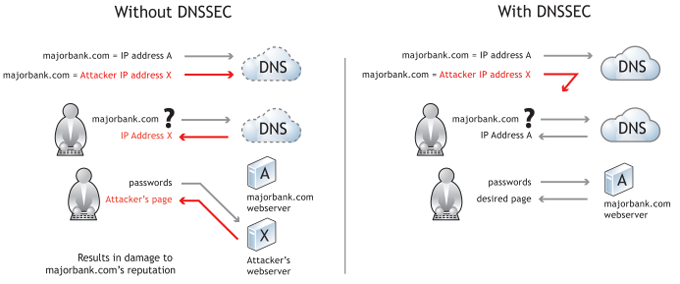
DNS was not designed with security in mind.
In the old days, the issue of trust, again, wasn't a problem. Almost anyone could run a name server and it be an authoritative leaf of the tree. The information each resolver supplied to another was rarely questioned, and assumed to be correct. There was no reason or motive to corrupt that information, or even doubt its authenticity. There was no reason to doubt the resolver you were contacting was anything else other than what it said it was.
But, computers met humanity. It became clear, quickly, the system could be "poisoned", intercepted, spoofed, and corrupted.
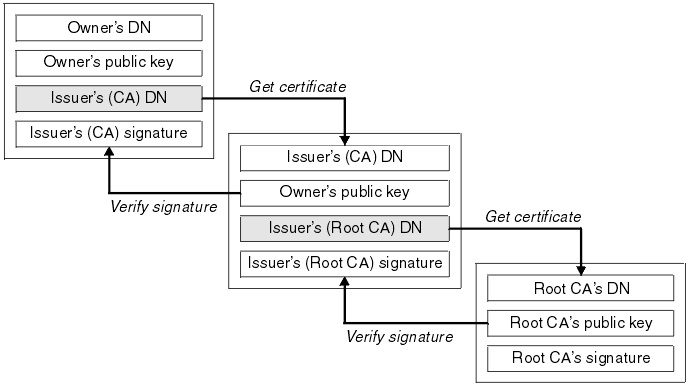
The answer was DNS Security Extensions (DNSSEC) which have a strong correlation with SSL:
- Data origin authentication allows a resolver to cryptographically verify that the data it received actually came from the zone where it believes the data originated.
- Data integrity protection allows the resolver to know that the data hasn't been modified in transit since it was originally signed by the zone owner with the zone's private key.
That still leaves the problem of needing to trust the actual cryptographic information. Back to the "root" issue we go.
As a commenter notes on StackExchange:
The problem with using Blockchain with domains, is that there's no inherent link between the domain and the keypair using for signing. So this information must be tied to each other somewhere. And somewhere would then be at the registrar, making the whole blockchain then useless as the registrar could then directly host the public key used for verifying — voilá — we reinvented the wheel: DNSSEC.
The blockchain is useful in 3 cases: Either, when you want to store public information, that can never be tampered with regards to time (time-stamping of information) or never be erased.
The third case would be where there's a inherent link between the domain and the key used for signing, that's what makes the system truly decentralized. But then we would get web addresses that look like TOR onion addresses. And TOR onion addresses is exactly this, hashes of public keys that makes it impossible to “forge” a site using a specific onion URL, and this can be validated without having to trust anyone.
To further illustrate the problem:
```
[secret data] = the private key
[public data] = the public key
[custom data] = your domain name or whatever name you want to associate with public key
```
There might be possible to create a process where you use some [secret data] + [custom data] to render a output of [custom data], but where [secret data] can be used in such a way that the corresponding [public data] can be programmatically related to [custom data] without having to trust anyone.
The only way I could come up with is a process like vanitygen, as if anyone can create a matching [secret data] for any [custom data], anyone could also “steal a domain name”.
That's why you need a trusted third-party, that will make this association, and make this association only for the person who owns the domain name in question, eg not allow this association for a domain name that is taken. So when it comes to domain names, you MUST trust somebody.
https://security.stackexchange.com/questions/131429/why-isnt-internet-dns-based-on-blockchain
What about SSL though? https://www.programmableweb.com/news/can-blockchain-replace-ssl/analysis/2015/03/17
Wait, This Isn't Just DNS
DNS isn't the only hierarchical trust system which is vulnerable to attack and provides a command and control resolution mechanism.
The other is digital certificates, which rely on a "chain" of 3rd party verifications all back to a central authority issuer (the root "trust anchor"). They are part of the X.509 standard, which defines how public key cryptography works within all the major parts of the Internet's functioning parts: HTTPS, CSRs, document signatures, and so on.
One group who picked this up were the okTurtles Foundation (https://okturtles.org/) who created their own answer to the problem: DNSChain.
"DNSChain deprecates today's insecure and fraudulent public key 1
infrastructure (PKI) by gracefully transitioning DNS from its hierarchical design, to one that is based on a globally distributed, peer-to-peer network that successfully "squares Zooko's triangle"
"DNSChain provides the missing “glue” to the Namecoin blockchain that makes it immediately accessible to clients of all types with zero configuration. A network administrator need only enter the IP address of a DNSChain-compliant DNS server to instantly make the information within the blockchain accessible to all of the users that she (or he) provides internet access to."
https://github.com/okTurtles/dnschain
https://okturtles.org/other/dnschain_okturtles_overview.pdf
https://en.wikipedia.org/wiki/Zooko%27s_triangle
They also provide a highly useful comparison of alternatives, detailing how they solve the triangle:
https://github.com/okTurtles/dnschain/blob/master/docs/Comparison.md
ZeroNet: Half-Finished & Half Thought-Out
Perhaps the most interesting candidate for a zero-knowledge system to date has been a Python experiment which combines the Blockchain with BitTorrent: ZeroNet (https://zeronet.io/). It's one of those pieces of tech which is so near genius it hurts to see it go wrong.

As the blurb states:
No single point of failure: Content remains online even if only one peer is serving it.
Impossible to shut down: It's nowhere because it's everywhere. Content is served by any user who wishes to.
ZeroNet turns every computer on the network into a host and a resolver. It works by providing a "middleman" server running on port 43110 of a person's computer, almost like an intranet. Users visit cryptographic site addresses and download the entire website using BitTorrent underneath onto their own machine, which they can then serve to other users. Anyone can create a site, and everyone who visits it then hosts a copy for everyone else. It takes an enormous effort to shut it down.
For the Pirate Bay and others, it's a panacea.
However, there are two massive problems with ZeroNet which have prevented its adoption:
- It's not available as a library for developers to include in their own software, and:
- Child porn.
Users who have visited ZeroNet sites have inadvertently gone on to sites which have been hosting content they didn't realise they were. Many of them have reported the sites being downloaded automatically onto their machines contained material so illegal it would only find a home in the darkest parts of Tor.
"While the peer-to-peer model is harder to take offline, it also turns 8chan users’ computers into hosts for the website. That means potentially downloading and redistributing content from the 8chan Zeronet site, which hosts a board called “Child Porn."
This is a problem i personally pointed out 4 years ago and was roundly dismissed for making, which sadly - and rather predictably - came true:
https://github.com/HelloZeroNet/ZeroNet/issues/252
Coins: Bringing In Wide-Scale Resolution
For all its many flaws, ZeroNet introduces an equally fascinating component to makes its domains easier to resolve: Namecoin's dotBIT address. It could take a while to elaborate, but the registrar's site does a tremendous job:
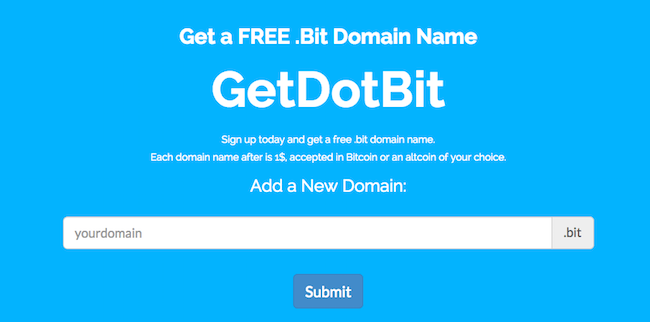
"Dot-Bit-enabled websites end with “.bit” instead of “.com” or something similar. Dot-Bit uses Bitcoin technology to decentralize and free website addresses, just like Bitcoin decentralizes and frees money.
Dot-Bit-enabled websites are immune to these problems [censorship etc], because instead of the phone book being a corporation or government, the digital phonebook is on your own computer. Bitcoin technology ensures that every user in the world has the same phonebook data on their computer, without anyone being able to illegitimately change that phonebook data.
https://www.namecoin.org/dot-bit/
NameCoin are fast becoming the new parents of the New Internet. For a good start, the theoretical combination with Ethereum certainly seems like a cosy fit:
- https://zmanian.github.io/namecoin_ethereum/#/7
- https://docs.blockstack.org/core/naming/introduction.html
Out of that network we have Handshake (https://handshake.org/) and the Ethereum Name Service (https://ens.domains/).

Summaries such as these abound: "A Comparative Study of Blockchain-Based DNS Design": https://dl.acm.org/doi/pdf/10.1145/3376044.3376057
Even Nominet UK is taking notice: https://www.nominet.uk/domain-names-unlock-new-potential-on-blockchain/
The New World is beginning to look quite a lot like the old one. For instance, instead of ICANN, we have IBCANN:
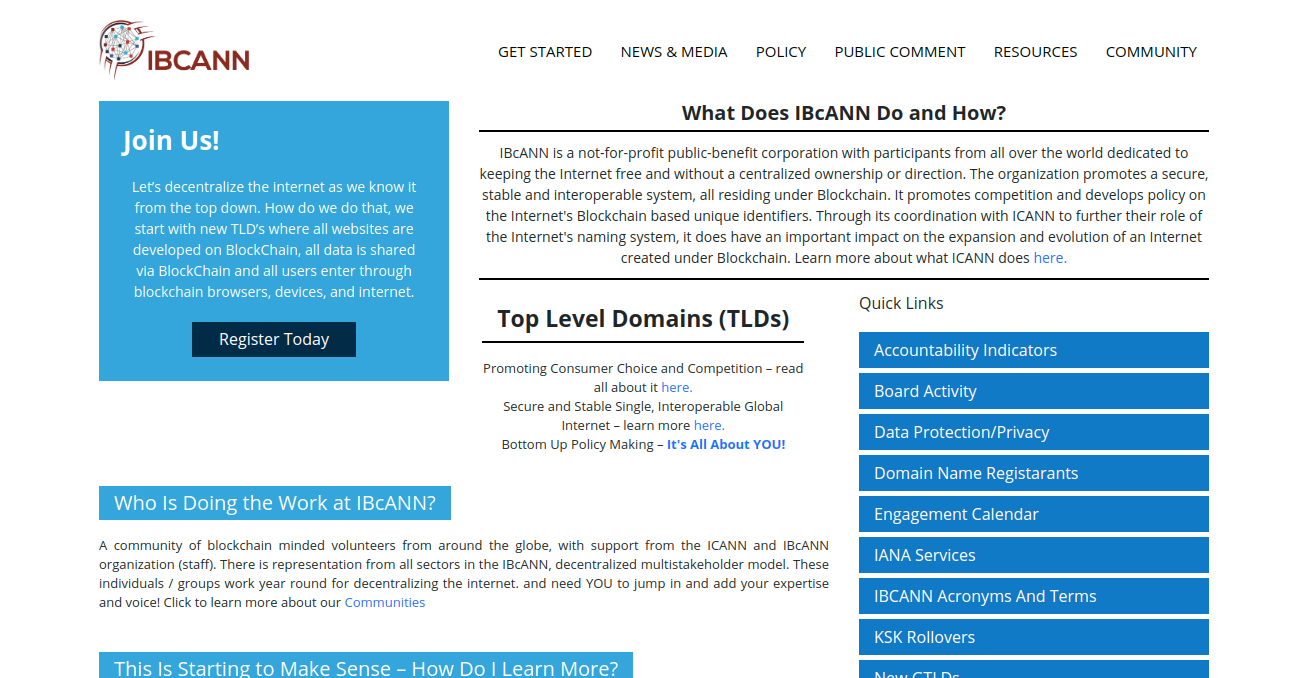
"IBcANN is a not-for-profit public-benefit corporation with participants from all over the world dedicated to keeping the Internet free and without a centralized ownership or direction. The organization promotes a secure, stable and interoperable system, all residing under Blockchain. It promotes competition and develops policy on the Internet's Blockchain based unique identifiers. Through its coordination with ICANN to further their role of the Internet's naming system, it does have an important impact on the expansion and evolution of an Internet created under Blockchain."
http://ibcann.org/
To register a new TLD (top-level domain), the most credible service still seems to be OpenNIC:
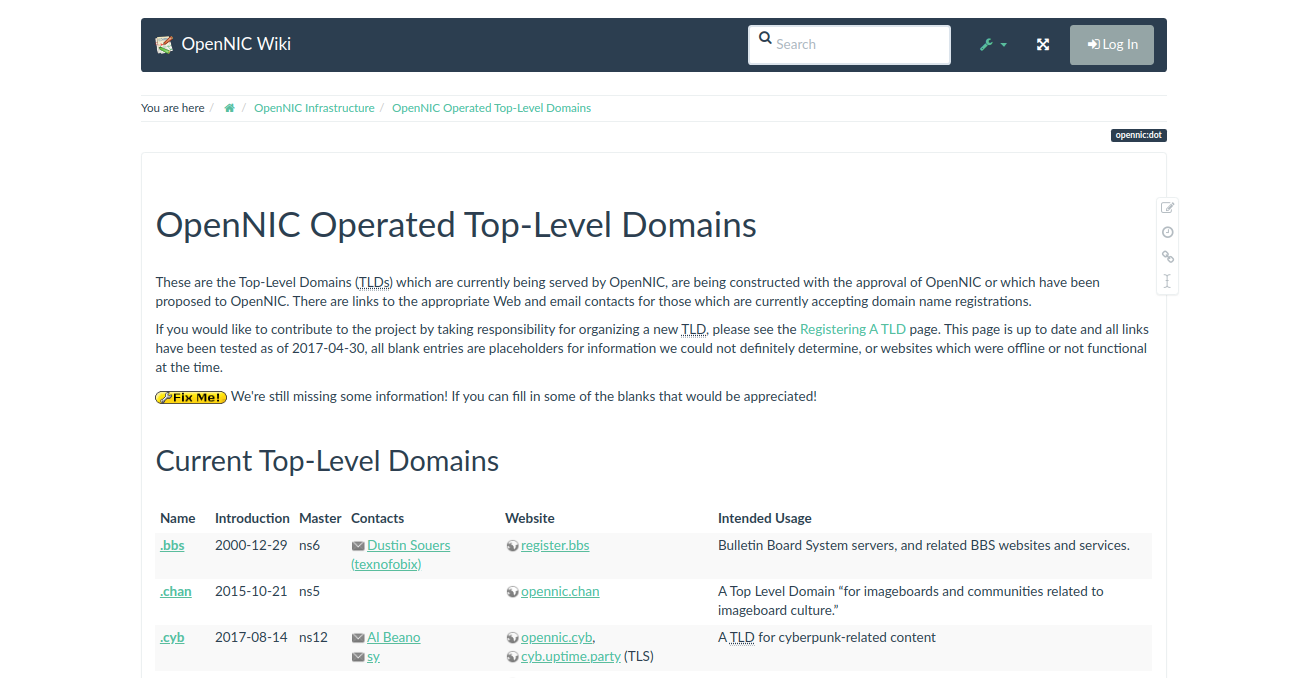
"OpenNIC (also referred to as the OpenNIC Project) is a user owned and controlled top-level Network Information Center offering a non-national alternative to traditional Top-Level Domain (TLD) registries; such as ICANN."
https://wiki.opennic.org/opennic/dot
And to put a lot of it together, there are GoDaddy-style registrar clones such as Chains Registry, Namebase, and PeerName:
Many of whom might like to use the blockchain version of BIND, helpfully called Blockname (https://github.com/telehash/blockname)
The Killer App required to mainstream blockchain-based DNS in the consumer world - if it's not supported by ISPs, are the browsers. Until then, it's necessary to use browser extensions to automatically resolve domains. Right now, the best-looking candidate is Blockchain-DNS.info, which despite being ugly, is rather well-formed:
https://blockchain-dns.info/explorer/
Many of these are to be auctioned off by providers who are looking to put the TLDs themselves on a blockchain to remove ICANN:
"The company’s most popular domain, for example, bitcoin.zil, has more than 500 prospective buyers looking to stake their claim to the prime web address. Rounding out the top five most in-demand domain names are “crypto,” “porn,” “blockchain” and “money.”
https://decrypt.co/7544/unstoppable-domains-auction-first-batch-uncensorable-web-domains?ref=hackernoon.com
Caveat Emptor...
Not to end on a dark note, but as always, where there are new ideas, there are bad people.
"AVCs and other sites used to trade stolen account information have been experimenting with peer-to-peer DNS technology in order to hide malicious activity and, crucially, bullet-proof their platforms. Jokers’ Stash was not the first to experiment with decentralized DNS, a group known as The Money Team also created a .bazar domain back in January 2016, again in an attempt to better secure their operations. As blockchain domains do not have a central authority and registrations contain unique encrypted hashes rather than an individual’s name and address, it is harder for law enforcement to perform site takedowns."
- https://www.digitalshadows.com/blog-and-research/how-cybercriminals-are-using-blockchain-dns-from-the-market-to-the-bazar/
- https://www.zdnet.com/article/opennic-drops-support-for-bit-domain-names-after-rampant-malware-abuse/
- "Unravelling Ariadne’s Thread: Exploring the Threats of Decentalised [sic] DNS": https://arxiv.org/pdf/1912.03552.pdf
