Can We Adapt Blockchain Tech For Direct Democracy Electoral Voting?

We have reached a place where democratic representatives in Western countries are members of country club aristocracies entirely disconnected from the public. Cryptographic technology and smartphones put us within reach of instant referenda polling for the first time.
If we can vote instantly, what need do we have of representatives who ignore us and cast their votes in opposition to their constituents' wishes? If we can get rid of them, why shouldn't we?
Direct Vs. Representative Democracy
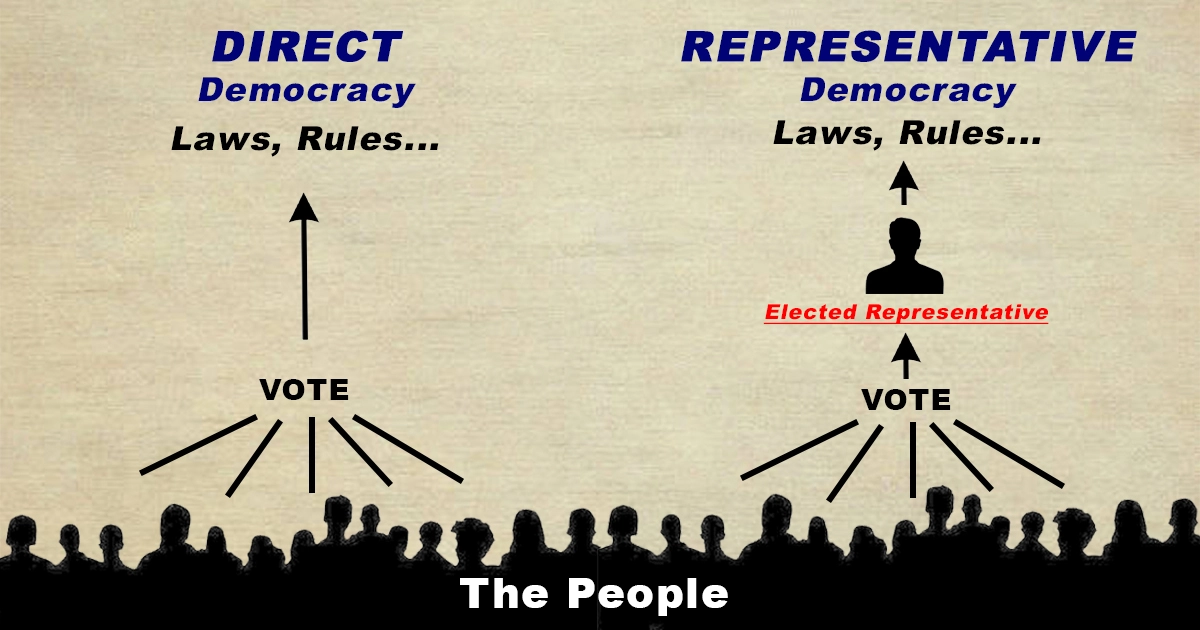
Direct democracy is a form of governance in which citizens directly participate in decision-making processes, usually by voting on policies, laws, or referendums. It stands in contrast to representative democracy, where citizens elect representatives who make decisions on their behalf.
While no country operates entirely on direct democracy principles, several countries have incorporated elements of direct democracy into their political systems. Switzerland is the most notable example, with its extensive use of referendums and popular initiatives at the federal, cantonal, and municipal levels. Other countries that use some elements of direct democracy include the United States (in some states), Germany, Ireland, and Italy, among others.
Pros of direct democracy:
- Increased citizen engagement: Direct democracy encourages citizens to be more involved in the decision-making process, leading to greater civic engagement and political awareness.
- More responsive governance: By giving citizens a direct say in decisions, direct democracy can make the government more responsive to the will of the people.
- Reduced influence of special interest groups: Direct democracy can diminish the influence of special interest groups on the legislative process, as citizens have the final say on policy decisions.
- Greater legitimacy: Decisions made through direct democracy may be perceived as more legitimate since they are made directly by the citizens affected by them.
Cons of direct democracy:
- Potential for uninformed decisions: Direct democracy relies on citizens being knowledgeable about the issues they are voting on, which may not always be the case. Uninformed decisions could lead to suboptimal policy outcomes.
- Risk of tyranny of the majority: Direct democracy can lead to decisions that favor the majority at the expense of minority rights or interests.
- Short-term focus: Direct democracy may encourage a short-term focus on immediate issues, rather than long-term strategic planning or consideration of complex issues.
- Administrative challenges: Implementing direct democracy on a large scale can be logistically challenging and resource-intensive, especially in countries with large populations.
Representative democracy, on the other hand, is a system in which citizens elect representatives to make decisions on their behalf. This approach has its own advantages and disadvantages.
Pros of representative democracy:
- Expertise and specialization: Elected representatives can develop expertise in specific policy areas, enabling them to make more informed decisions than the general public.
- Efficient decision-making: Representative democracy allows for efficient decision-making processes, as representatives can dedicate their time to considering complex issues and making decisions.
- Protection of minority rights: Elected representatives can act as a check against the tyranny of the majority by considering the interests of all citizens, including minority groups.
- Long-term focus: Representatives can focus on long-term policy planning and address complex issues that may be challenging for citizens to understand fully.
Cons of representative democracy:
- Influence of special interest groups: Elected representatives may be susceptible to lobbying or influence from special interest groups, leading to decisions that do not reflect the will of the people.
- Limited citizen engagement: Representative democracy can result in lower levels of political engagement and awareness among citizens, as they are not directly involved in the decision-making process.
- Risk of corruption: The concentration of power in the hands of elected representatives can create opportunities for corruption and abuse of power.
Direct democracy and representative democracy each have their own advantages and drawbacks. While direct democracy offers greater citizen involvement and responsiveness, it may also lead to uninformed decisions and challenges in protecting minority rights.
Representative democracy provides expertise and efficient decision-making but may be more susceptible to the influence of special interest groups and corruption. Many countries have adopted hybrid systems that combine elements of both direct and representative democracy to balance these trade-offs.
Why Would We Want To Change?
A shared ledger blockchain system can help facilitate the transition from a representative democracy to a direct democracy and referenda-based system by enabling secure, transparent, and efficient voting processes for both legislative decision-making and public policy issues.
Why? Because we can. Technology has changed the game.
Legislative voting
In a direct democracy, citizens would have the opportunity to vote on legislative proposals directly, rather than relying on elected representatives to make decisions on their behalf. A blockchain-based system could be used to enable citizens to securely cast their votes on specific bills and policy proposals. This would allow for more direct participation in the legislative process and greater influence over the laws that govern society.
Referenda
A blockchain-based system could facilitate the organization and execution of referenda on key policy issues. Citizens could propose and vote on initiatives, and the results would be recorded securely and transparently on the blockchain. This would empower citizens to have a more direct say in important matters affecting their lives and communities.
Decentralised Decision-Making
A blockchain-based voting system could also be used to enable decentralised decision-making at various levels of governance, such as local, regional, and national levels. This could promote more responsive and participatory governance, as citizens would have a direct voice in decisions that impact their communities.
Transparency and Accountability
The use of a shared ledger in a blockchain system would provide a transparent and auditable record of all voting transactions. This would help ensure the integrity of the voting process, reduce the potential for fraud or manipulation, and increase overall trust in the democratic system.
Improved Civic Engagement
By providing a secure and user-friendly platform for voting on legislative proposals and referenda, a blockchain-based system could encourage greater civic engagement and political participation among citizens. This would help create a more informed and active electorate, ultimately strengthening the democratic process.
Cost Reduction and Efficiency
The use of blockchain technology could reduce the costs associated with traditional voting methods, such as paper ballots and physical polling stations. By leveraging a digital platform, the administration and execution of direct democracy and referenda processes could become more efficient and cost-effective.
Advantages To Decentralising
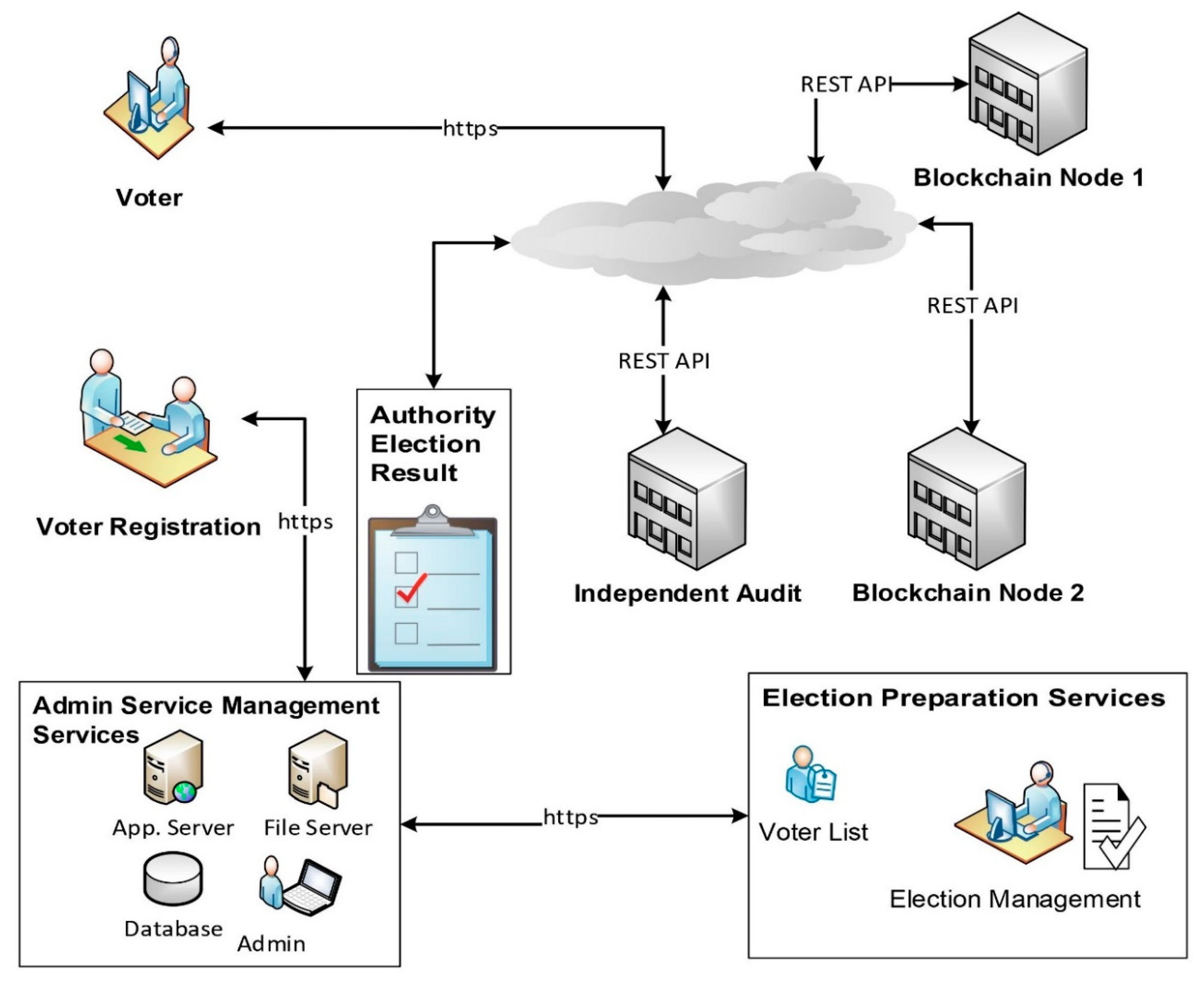
A blockchain-based voting system can help minimize the role or presence of a centralized electoral authority by decentralising the election process and making it more transparent and auditable. However, it is important to note that some form of oversight will always be necessary to ensure the integrity of the election process.
Decentralised Voter Registration
Voter registration could be managed using a decentralised and transparent process. This may involve a secure and auditable digital identity system that is not controlled by a single entity. The system could be built on a blockchain platform to ensure transparency, security, and integrity.
Decentralised Vote Casting
Blockchain technology can enable a decentralised voting system where votes are cast and recorded on a distributed ledger. This eliminates the need for a centralized authority to manage and control the voting process. Voters can cast their votes using secure cryptographic techniques, ensuring that the votes are valid and tamper-proof.
Decentralised Vote Counting and Tallying
In a blockchain-based voting system, vote counting and tallying can be performed automatically by the network, reducing the need for a centralized authority to oversee these processes. The use of smart contracts can further automate the process of counting and validating votes, ensuring accuracy and transparency.
Decentralised Auditing and Monitoring
A decentralised voting system can be designed to allow third-party organizations, such as non-governmental organizations, international observers, or independent auditors, to monitor the election process and verify the results. This can be achieved by providing public access to the blockchain ledger, allowing external parties to review and audit the election process without the need for a centralized electoral authority.
Consensus-based Dispute Resolution
In the event of a dispute or challenge to the legitimacy of election results, a consensus-based dispute resolution mechanism can be implemented. This may involve a combination of human arbitration and automated processes, such as using smart contracts to analyze and verify the integrity of the voting data. In this way, disputes can be resolved transparently and impartially, without the need for centralized authorities to intervene.
And the Problems?
There are no solutions; only trade-offs. Direct democracy isn't a panacea, and neither is Blockchain tech.
- Digital divide: Not everyone has access to the internet or digital devices, which may lead to exclusion or unequal participation in the election process.
- Voter anonymity: One of the key principles of a democratic election is the secrecy of the ballot. Preserving voter anonymity while ensuring the transparency and integrity of the system can be a challenge in a blockchain-based voting system.
- Scalability: During a national election, millions of people will cast their votes simultaneously. Blockchain networks may struggle to handle such a large volume of transactions, leading to slow processing times and possible network congestion.
- Security: While blockchains are generally secure, they are not impervious to attacks. There is a risk of 51% attacks, where a single entity gains control over more than half of the network's mining power, potentially allowing them to manipulate the voting results.
- Legal and regulatory barriers: Implementing a blockchain-based voting system may require changes in existing election laws and regulations, which can be time-consuming and politically challenging.
- Public trust: Citizens must trust the technology and be confident in its ability to accurately and securely record their votes. Any doubts or confusion may undermine the legitimacy of the election results.
- Technical complexity: A national election involves a complex system of voting machines, registration databases, and vote counting processes. Integrating a blockchain-based system with these existing components while maintaining security and transparency could be challenging.
- Cost: Developing, implementing, and maintaining a blockchain-based voting system could be expensive. It may require significant investment in infrastructure, software, and training for election officials.
- Auditing and dispute resolution: In the case of disputes or allegations of fraud, it may be challenging to audit and verify the election results on a blockchain system. Furthermore, establishing an effective dispute resolution process is crucial for maintaining public trust in the electoral process.
- Resistance to change: Implementing a blockchain-based voting system would require a significant shift in the way elections are conducted. This could face resistance from election officials, political parties, and other stakeholders who may be reluctant to adopt new technologies or change the existing system.
Against: MIT & Scientific American, the Cathedral
Blockchain voting would require more than simply replacing Bitcoin transactions with votes. “Bitcoin works because you don’t need [centrally issued] identities,” says Arthur Gervais, a blockchain researcher at University College London. Instead, users generate public “addresses,” which act like deposit-only account numbers for receiving money, along with secret digital “keys” that are needed to transfer money out of the corresponding accounts. Anyone can create key-address pairs willy-nilly.
"Are Blockchains the Answer for Secure Elections? Probably Not"
https://www.scientificamerican.com/article/are-blockchains-the-answer-for-secure-elections-probably-not/
Researchers at MIT are much more sceptical:
1. Blockchain technology does not solve the fundamental security problems suffered by all electronic voting systems. Moreover, blockchains may introduce new problems that nonblockchain-based voting systems would not suffer from.
2. Electronic, online, and blockchain-based voting systems are more vulnerable to serious failures than available paper-ballot-based alternatives. Moreover, given the state of the art in computer security, they will continue to be so for the foreseeable future.
3. Adding new technologies to systems may create new potential for attacks. Particular caution is appropriate in security-critical applications, especially where political pressures may favor an expedited approach.
"Going from Bad to Worse: From Internet Voting to Blockchain Voting"
(Ron Rivest, MIT Computer Science and Artificial Intelligence Laboratory (CSAIL) professor and one of the creators of RSA encryption; Michael Specter; Sunoo Park; and Director of MIT’s Digital Currency Initiative (DCI) Neha Narula.)
https://people.csail.mit.edu/rivest/pubs/PSNR20.pdf
How Might It Work?
A blockchain-based voting system would leverage distributed ledger technology to record, verify, and store votes in a secure and transparent manner - hopefully.
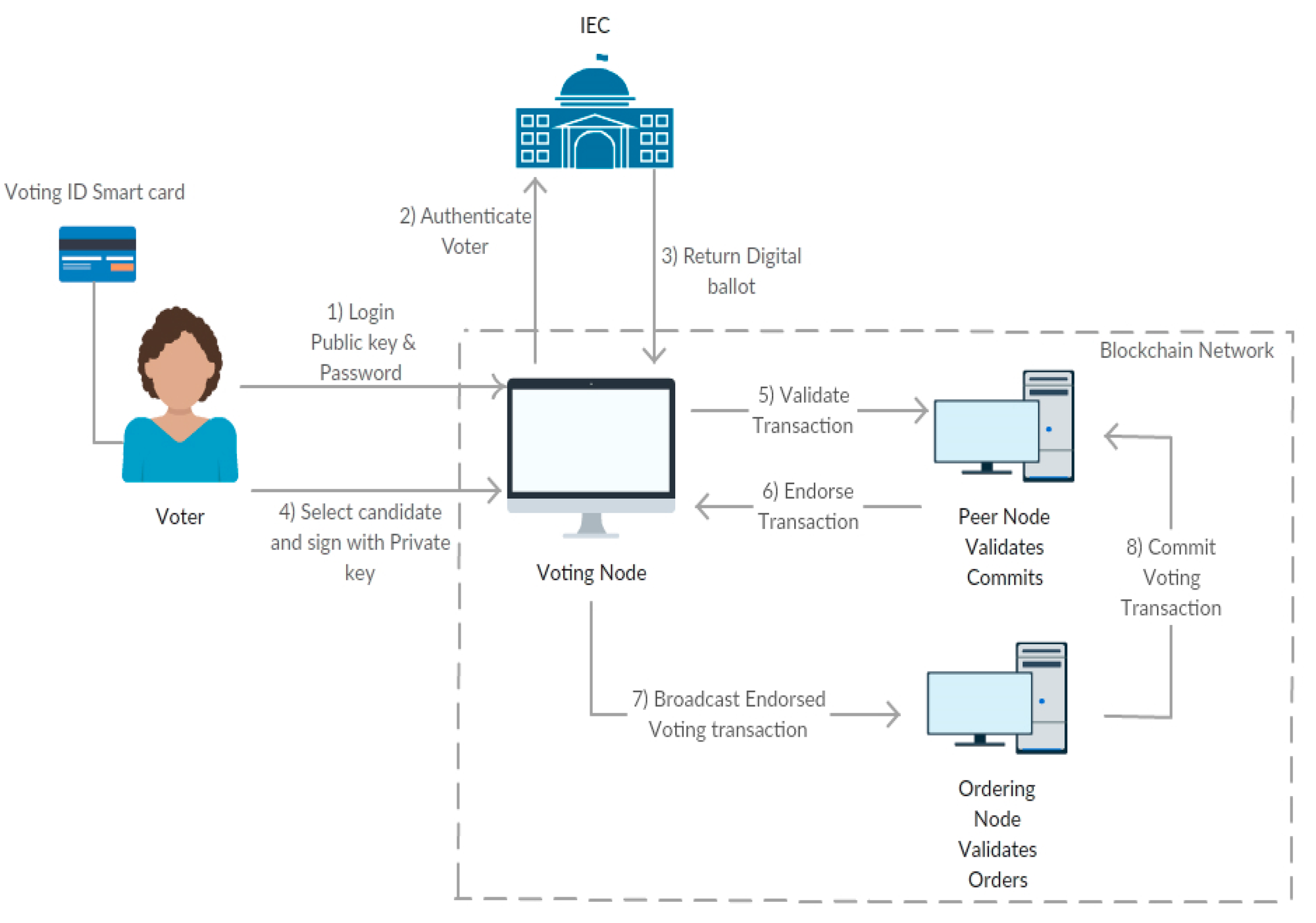
Voter registration and authentication
Before casting a vote, each voter would need to register and be authenticated. This could be achieved through a combination of traditional methods and digital identity solutions such as biometrics or digital certificates. A secure, tamper-proof record of eligible voters can be maintained on the blockchain.
Reference: Kiayias, A., Koutsoupias, E., Kyropoulou, M., & Tselekounis, Y. (2016). Blockchain in voting and elections. IACR Cryptology ePrint Archive, 2016, 300.
Vote Casting
Once authenticated, voters would receive a unique, encrypted digital token representing their vote.
Voters would use a secure, user-friendly voting application on their smartphones or dedicated devices at a polling station. The application would provide a list of candidates, parties, or referenda options for the voter to choose from.
Once a voter makes their selection, the vote would be encrypted and digitally signed using the voter's private key. This ensures the vote's confidentiality and integrity, as well as allowing for verification of the voter's identity without revealing their choice.
The encrypted and digitally signed vote would be submitted to the blockchain network, where it would be verified and added to the ledger as a new transaction. This process would ensure that the vote is securely recorded and that only eligible, authenticated voters can participate in the election.
Voters would receive a confirmation receipt, which could be used to verify that their vote was successfully submitted and recorded on the blockchain. This receipt would not reveal the voter's choice, preserving the secrecy of the ballot.
Reference: McCorry, P., Shahandashti, S. F., & Hao, F. (2017). A smart contract for boardroom voting with maximum voter privacy. In International Conference on Financial Cryptography and Data Security (pp. 357-375). Springer, Cham.
Vote Verification and Storage
As votes are cast, they would be verified by nodes within the blockchain network, ensuring that each vote is valid and comes from a registered voter. Verified votes would then be added to the blockchain in the form of blocks, creating an immutable, transparent, and auditable record of all votes.
Reference: Noizat, P. (2015). Blockchain Electronic Vote. In 2015 2nd IEEE International Conference on Cyber Security and Cloud Computing (pp. 518-523). IEEE.
Vote Tallying and Result Announcement
Once the voting period is over, the encrypted votes stored on the blockchain can be decrypted and tallied using a secure multi-party computation or homomorphic encryption techniques. This would allow for the accurate determination of the election results without revealing individual voter's choices.
Reference: Bistarelli, S., Santancini, P., & Santini, F. (2017). A blockchain-based approach for the definition of auditable access control systems. In Proceedings of the 12th International Conference on Availability, Reliability and Security (pp. 68-73). ACM.
Auditing and Dispute Resolution
n the case of disputes, the transparent and tamper-proof nature of the blockchain allows for efficient auditing of the voting process. This can help in validating the election results and resolving any disputes or allegations of fraud.
Reference: Hardwick, F., Akram, R. N., & Markantonakis, K. (2018). Electronic voting with fully distributed trust using blockchain. In 2018 IEEE International Conference on Internet of Things (iThings) and IEEE Green Computing and Communications (GreenCom) and IEEE Cyber, Physical and Social Computing (CPSCom) and IEEE Smart Data (SmartData) (pp. 1560-1567). IEEE.
In case a person's voting credentials are lost or stolen, there would need to be a secure process in place for credential recovery or replacement:
- Reporting loss or theft: Voters would report the loss or theft of their voting credentials to the appropriate election authority, providing necessary identification details to verify their identity.
- Revoking compromised credentials: The election authority would revoke the compromised credentials, preventing unauthorized use or voting on behalf of the legitimate voter.
- Issuing new credentials: After verifying the voter's identity, the election authority would issue new credentials, such as a new private key or digital certificate, to the voter. The voter would need to securely store these new credentials and use them to authenticate and cast their vote in the election.
- Monitoring for fraud: The election authority would need to monitor the system for any signs of fraudulent activity related to lost or stolen credentials, such as multiple votes being cast with the same credentials, to ensure the integrity of the voting process.
ZK-SNARK: Enhanced Privacy
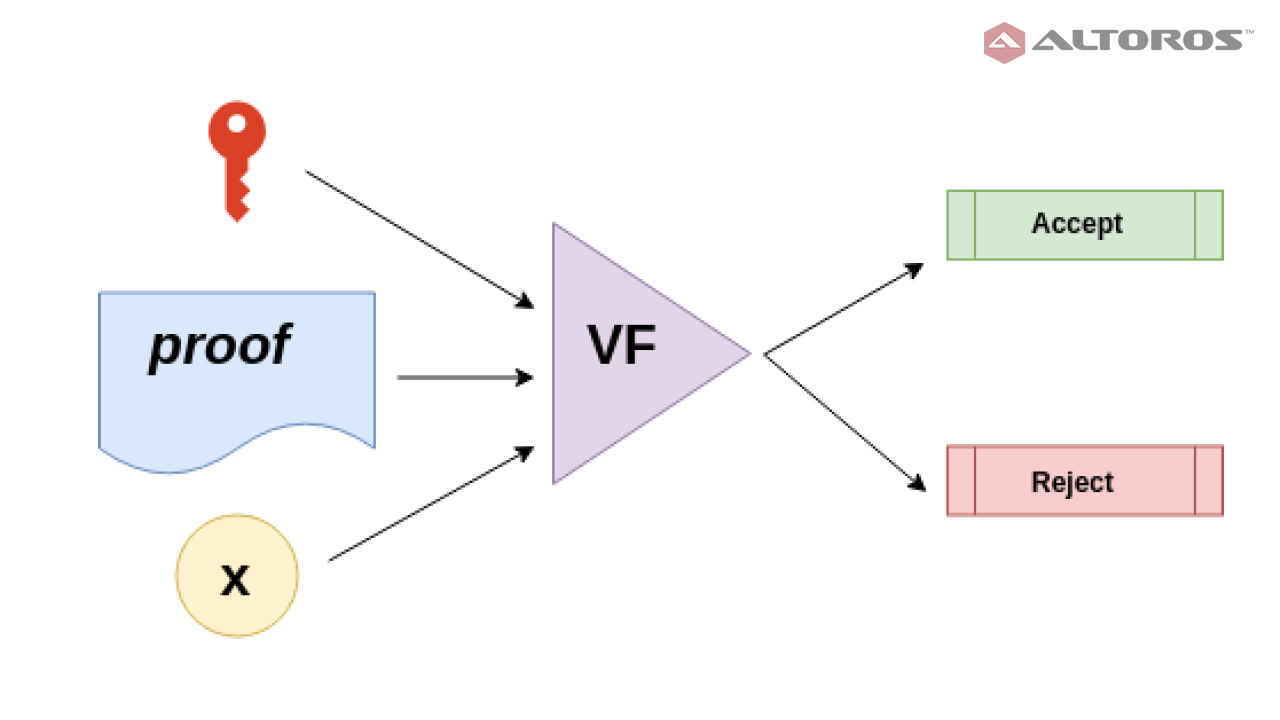
ZK-SNARK (Zero-Knowledge Succinct Non-Interactive Argument of Knowledge) is a cryptographic technique that enables one party to prove the possession of certain information without revealing the information itself. In a voting system, ZK-SNARK can play a crucial role in preserving voter privacy while ensuring the validity and accuracy of the voting process.
Anonymity and Privacy
ZK-SNARK allows voters to prove they are eligible to vote without revealing their identity or any personally identifiable information. This ensures that the voter's privacy is maintained while still enabling the verification of the voter's eligibility. In the context of a blockchain-based voting system, ZK-SNARK allows a voter to prove that their vote was correctly recorded and tallied without revealing their actual vote or any identifying details.
Voter Coercion and Vote Selling Prevention
By preserving voter privacy and maintaining the secrecy of individual votes, ZK-SNARK makes it more difficult for bad actors to coerce voters or buy their votes. Since voters can vote anonymously and their choices are not revealed, there is no way for a coercer or vote buyer to verify how a person voted, making coercion and vote buying less effective.
Efficient Verification
ZK-SNARKs are designed to be computationally efficient, allowing for quick and resource-efficient verification of proofs. This is particularly useful in a voting system, where potentially millions of votes need to be verified and tallied in a timely manner. The efficiency of ZK-SNARKs enables the system to handle large-scale elections without significant delays or computational overhead.
Non-interactive Proofs
ZK-SNARK is a non-interactive zero-knowledge proof, which means that the prover and verifier do not need to engage in a back-and-forth communication to validate the proof. This simplifies the verification process and reduces the potential for errors or manipulation in the voting system.
Tamper-proof Records
ZK-SNARK can be combined with blockchain technology to create a secure, tamper-proof record of votes. The use of zero-knowledge proofs ensures that each vote is valid and accurately recorded while maintaining voter privacy. This creates a transparent and auditable voting process that is resistant to tampering, fraud, or manipulation.
Electoral Fraud: Detection, Prevention, Prosecution
Electoral fraud vote rigging is as old as Athens. It is in every election, every time. The only question is how extensive it is.
For example, the New York Post detailed how severe this problem is:
The whisteblower — whose identity, rap sheet and long history working as a consultant to various campaigns were confirmed by The Post — says he not only changed ballots himself over the years, but led teams of fraudsters and mentored at least 20 operatives in New Jersey, New York and Pennsylvania — a critical 2020 swing state.
"Confessions of a voter fraud: I was a master at fixing mail-in ballots"
https://nypost.com/2020/08/29/political-insider-explains-voter-fraud-with-mail-in-ballots/
Government/Party Fraud
- Voter registration manipulation: A government could manipulate the voter registration process, adding or removing voters from the list to influence the election outcome. This could be done by adding ineligible voters, removing eligible ones, or changing voter information.
- Digital identity abuse: If a government controls the digital identity system used for voter authentication, it could forge digital identities or issue multiple identities to the same individual, enabling them to cast multiple votes.
- Centralisation of power: If a government controls a significant portion of the nodes within the blockchain network, it could potentially gain control over the voting process, manipulate vote tallies, or compromise the integrity of the system. This could be achieved through a 51% attack, as previously mentioned.
- Code vulnerabilities: A government could introduce vulnerabilities or backdoors into the voting system's software, allowing it to manipulate the system undetected. This could involve modifying the vote tallying process, compromising voter privacy, or tampering with the blockchain records.
- Voter coercion and vote-buying: In a blockchain-based system, if voter privacy is not adequately protected, a government could potentially trace votes back to individual voters. This could enable voter coercion or vote-buying, undermining the principle of a secret ballot.
- Disinformation campaigns: A government could spread disinformation about the security, reliability, or accuracy of the blockchain-based voting system to undermine public trust in the electoral process, potentially swaying the election outcome.
- Disruption of network infrastructure: A government could interfere with the network infrastructure, such as internet connectivity or power supplies, to disrupt the voting process and prevent certain groups of voters from participating in the election.
Party/Bad Actor Fraud
- Sybil attacks: Bad actors could create multiple fake identities to register as eligible voters, undermining the integrity of the voter registration process and allowing them to cast multiple fraudulent votes.
- Exploiting code vulnerabilities: If the voting system's software has vulnerabilities or weak security measures, bad actors could exploit them to manipulate the system, tamper with vote tallies, or compromise voter privacy.
- Social engineering attacks: Bad actors could use social engineering tactics, such as phishing, to trick voters into revealing their voting credentials, allowing them to cast fraudulent votes on the victims' behalf.
- Voter coercion or vote-buying: If voter privacy is not adequately protected, bad actors could potentially trace votes back to individual voters, enabling voter coercion or vote-buying schemes.
- Disinformation campaigns: Bad actors could spread false information or disinformation about the security, reliability, or accuracy of the blockchain-based voting system to undermine public trust in the electoral process or sway public opinion.
- Cyberattacks: Malicious entities could launch distributed denial-of-service (DDoS) attacks or other cyberattacks to disrupt the voting system's infrastructure or internet connectivity, preventing or hindering voters from participating in the election.
- Collusion with insiders: Bad actors could collude with insiders, such as developers, election officials, or operators of blockchain nodes, to introduce vulnerabilities, manipulate the voting process, or gain unauthorized access to sensitive information.
Adapting Traditional Fraud To Blockchain Tech
Times change, we change with the times. The same old behaviour will always appear. The question becomes... how?
Voter Coercion and Vote Buying:
- Traditional: Bad actors exert pressure on voters or offer incentives to vote for a specific candidate or party.
- Adaptation: Although blockchain voting systems can provide anonymity and privacy, bad actors could still coerce voters by monitoring their physical environment while voting (e.g., through cameras or in-person observation) or by leveraging social engineering techniques to obtain proof of a specific vote.
Impersonation and Identity Theft:
- Traditional: Bad actors impersonate eligible voters and cast votes on their behalf.
- Adaptation: If the digital identity system linked to the blockchain-based voting system is compromised, bad actors might be able to steal the digital identities of legitimate voters and cast fraudulent votes using their credentials.
Denial of Service:
- Traditional: Overloading polling stations or disrupting the voting process to prevent eligible voters from casting their votes.
- Adaptation: Bad actors could target the infrastructure of the blockchain voting system (e.g., servers, nodes, or network connections) with distributed denial of service (DDoS) attacks, making it difficult for voters to access the system and cast their votes.
Voter Suppression:
- Traditional: Implementing policies or spreading misinformation to discourage or prevent certain groups of voters from participating in the election.
- Adaptation: Bad actors could spread misinformation about the blockchain voting system, create confusion about the voting process, or exploit weaknesses in the system's user interface to discourage or prevent specific groups from voting.
Vote Manipulation or Tampering:
- Traditional: Altering or manipulating vote counts to favor a specific candidate or party.
- Adaptation: While blockchain technology provides a secure and tamper-proof record of votes, it is not completely immune to attacks. A well-resourced bad actor could attempt to execute a 51% attack on the blockchain network, allowing them to manipulate the vote count. However, such an attack would be difficult and costly to carry out, especially on a large-scale, well-secured blockchain network.
Exploiting software vulnerabilities:
- Traditional: Exploiting weaknesses or vulnerabilities in the voting system's software to alter vote counts or disrupt the voting process.
- Adaptation: Bad actors could exploit vulnerabilities in the blockchain voting system's software or smart contracts to alter votes, manipulate vote counts, or disrupt the voting process.
In addition, smartphones have their own problems:
- Device security: Smartphones can be susceptible to malware, viruses, and other security threats that could compromise the integrity of the voting process. Hackers could potentially target voters' devices to steal their credentials, alter their votes, or disrupt the voting process.
- Phishing attacks: Bad actors could create fake voting apps or websites designed to steal voters' credentials or trick them into revealing sensitive information. Unsuspecting users might be directed to these malicious platforms through social engineering techniques, such as phishing emails, text messages, or social media posts.
- User error: Some users may not follow security best practices, such as using strong passwords, enabling two-factor authentication, or keeping their devices and apps up to date. This could make it easier for bad actors to compromise their devices and exploit the voting process.
- Network security: Public Wi-Fi networks and cellular connections can be vulnerable to attacks, such as man-in-the-middle attacks, which could compromise the data transmitted between the voter's device and the blockchain voting system. This could lead to the interception, alteration, or deletion of votes.
References & Further Reading
- Kiayias, A., Koutsoupias, E., Kyropoulou, M., & Tselekounis, Y. (2016). Blockchain in voting and elections. IACR Cryptology ePrint Archive, 2016, 300.
- McCorry, P., Shahandashti, S. F., & Hao, F. (2017). A smart contract for boardroom voting with maximum voter privacy. In International Conference on Financial Cryptography and Data Security (pp. 357-375). Springer, Cham. https://link.springer.com/chapter/10.1007/978-3-319-70972-7_20
- Noizat, P. (2015). Blockchain Electronic Vote. In 2015 2nd IEEE International Conference on Cyber Security and Cloud Computing (pp. 518-523). IEEE. https://www.sciencedirect.com/science/article/abs/pii/B9780128021170000229
- Bistarelli, S., Santancini, P., & Santini, F. (2017). A blockchain-based approach for the definition of auditable access control systems. In Proceedings of the 12th International Conference on Availability, Reliability and Security (pp. 68-73). ACM. https://www.sciencedirect.com/science/article/abs/pii/S0167404818309398
- Hardwick, F., Akram, R. N., & Markantonakis, K. (2018). Electronic voting with fully distributed trust using blockchain. In 2018 IEEE International Conference on Internet of Things (iThings) and IEEE Green Computing and Communications (GreenCom) and IEEE Cyber, Physical and Social Computing (CPSCom) and IEEE Smart Data (SmartData) (pp. 1560-1567). IEEE.
- Rana, S., & Verma, S. (2017). Electronic voting system using Ethereum blockchain. In 2017 1st India International Conference on Information Processing (IICIP) (pp. 1-4). IEEE.
- Osgood, R. (2017). The future of voting: Potential for blockchain technology in electronic voting systems. In 2017 IEEE MIT Undergraduate Research Technology Conference (URTC) (pp. 1-4). IEEE.
- Ali, M. S., Vecna, N., & Cascudo, P. (2017). Applications of secure multi-party computation. In IACR Cryptology ePrint Archive, 2017, 623.
- Bracamonte, V., & Okamoto, T. (2017). An e-voting scheme based on blockchain and ring signature. In 2017 19th International Conference on Advanced Communication Technology (ICACT) (pp. 464-467). IEEE.
- Meng, J., & Wang, W. (2017). Secure electronic voting system based on blockchain. In 2017 International Conference on Security, Pattern Analysis, and Cybernetics (SPAC) (pp. 433-436). IEEE.
- Dagher, G. G., Mohler, J., Milojkovic, M., & Marella, P. B. (2018). Ancile: Privacy-preserving framework for access control and interoperability of electronic health records using blockchain technology. Sustainable Cities and Society, 39, 283-297. https://www.researchgate.net/publication/323247610_Ancile_Privacy-preserving_Framework_for_Access_Control_and_Interoperability_of_Electronic_Health_Records_Using_Blockchain_Technology
- Hao, F., & Zieliński, P. (2018). A 2-round anonymous veto protocol. In International Conference on Financial Cryptography and Data Security (pp. 202-213). Springer, Berlin, Heidelberg.
- Ribeiro, M., & Pontes, R. (2018). Crypto-voting: A new voting system based on blockchain technology. In 2018 IEEE 17th International Symposium on Network Computing and Applications (NCA) (pp. 1-6). IEEE.
- Hjálmarsson, F., Hreiðarsson, G. K., Hamdaqa, M., & Hjaltason, H. (2018). Blockchain-based e-voting system. In 2018 IEEE 11th International Conference on Cloud Computing (CLOUD) (pp. 983-986). IEEE.
- Vora, J., Nayyar, A., & Tanwar, S. (2019). Blockchain enabled e-voting recording system design. In 2019 11th International Conference on Communication Systems & Networks (COMSNETS) (pp. 556-560). IEEE.
- Chalaemwongwan, N., & Kurutach, W. (2019). A secure e-voting protocol based on Ethereum blockchain. In 2019 11th International Conference on Information Technology and Electrical Engineering (ICITEE) (pp. 1-6). IEEE.
- Bhattacherjee, S., Maity, S., & Nandi, S. (2019). Secure e-voting protocol using blockchain. In 2019 IEEE 16th India Council International Conference (INDICON) (pp. 1-6). IEEE.
- Ruelens, J., & Böhme, R. (2019). Making Voting Easier with the Blockchain: Design and Security Aspects of SecureVote. In Proceedings of the 1st Workshop on Cryptocurrencies and Blockchains for Distributed Systems (pp. 19-24). ACM.
- Matyukhin, M., & Shnurkov, M. (2019). Electronic voting systems based on blockchain technology. In 2019 IEEE Conference of Russian Young Researchers in Electrical and Electronic Engineering (EIConRus) (pp. 1255-1259). IEEE.
- Le, T. V. (2019). A survey on blockchain-based e-voting systems. In 2019 6th NAFOSTED Conference on Information and Computer Science (NICS) (pp. 268-273). IEEE. https://www.researchgate.net/publication/340081625_A_Survey_of_Blockchain_Based_on_E-voting_Systems
- Akca, M. S., & Yurdakul, A. (2019). Electronic voting systems based on blockchain. In 2019 International Conference on Computer Science and Engineering (UBMK) (pp. 59-63). IEEE.
- Tootoonchian, A., & Ganjali, Y. (2020). HyperService: Interoperability and programmability across heterogeneous blockchains. In Proceedings of the 17th ACM Workshop on Hot Topics in Networks (pp. 29-35). ACM. https://arxiv.org/abs/1908.09343
- Kshetri, N. (2020). Will blockchain emerge as a tool to break the poverty chain in the Global South? Third World Quarterly, 38(8), 1710-1732. https://libres.uncg.edu/ir/uncg/f/N_Kshetri_Will_2017.pdf
- Chen, J., Zhang, J., & Chen, J. (2020). A secure and efficient e-voting protocol based on blockchain. In 2020 IEEE 4th International Conference on Computer and Communication Systems (ICCCS) (pp. 1-5). IEEE.
- Puthal, D., Malik, N., Mohanty, S. P., Kougianos, E., & Das, G. (2020). The blockchain as a decentralized security framework [future directions]. IEEE Consumer Electronics Magazine, 7(2), 18-21. https://ieeexplore.ieee.org/document/8287055